-
- Downloads
kci-gitlab: Introducing GitLab-CI Pipeline for Kernel Testing
This patch introduces a `.gitlab-ci` file along with a `ci/` folder, defininga basic test pipeline triggered by code pushes to a GitLab-CI instance. This initial version includes static checks (checkpatch and smatch for now) and build tests across various architectures and configurations. It leverages an integrated cache for efficient build times and introduces a flexible 'scenarios' mechanism for subsystem-specific extensions. [ci: add prerequisites to run check-patch on MRs] Co-developed-by:Tales Aparecida <tales.aparecida@redhat.com> Signed-off-by:
Tales Aparecida <tales.aparecida@redhat.com> Signed-off-by:
Helen Koike <helen.koike@collabora.com> --- KCI_PATCH_SERIES_SIZE=1
Showing
- .gitlab-ci.yml 2 additions, 0 deletions.gitlab-ci.yml
- Documentation/ci/gitlab-ci/gitlab-ci.rst 404 additions, 0 deletionsDocumentation/ci/gitlab-ci/gitlab-ci.rst
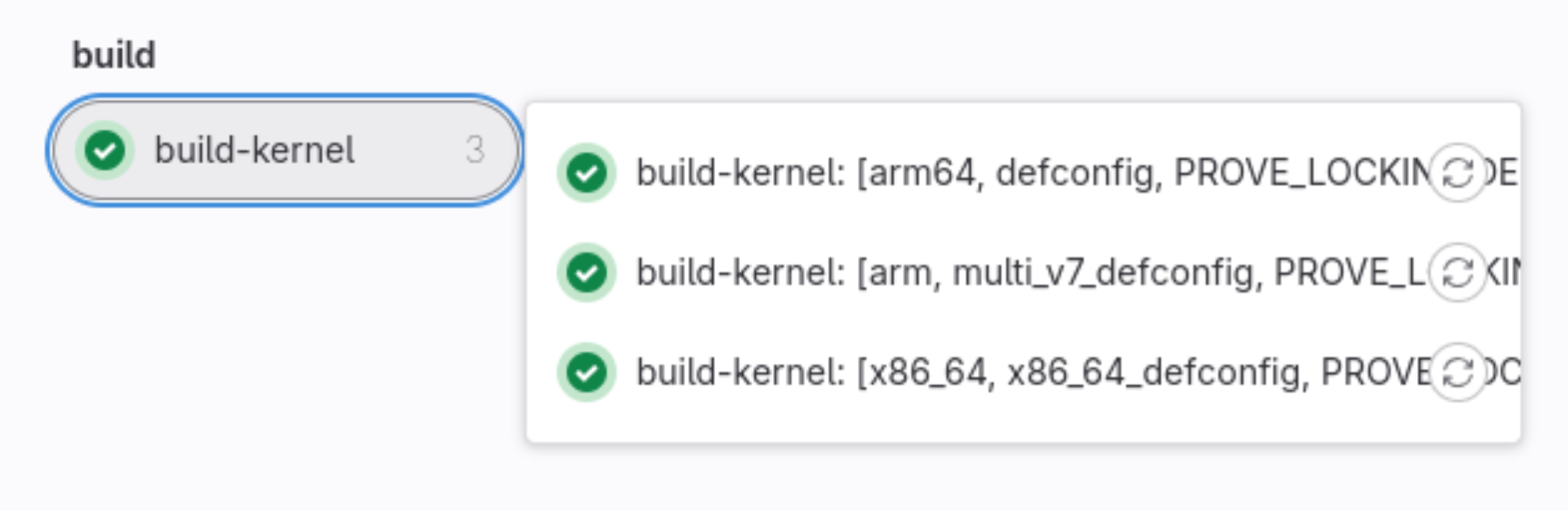
- Documentation/ci/gitlab-ci/images/job-matrix.png 0 additions, 0 deletionsDocumentation/ci/gitlab-ci/images/job-matrix.png
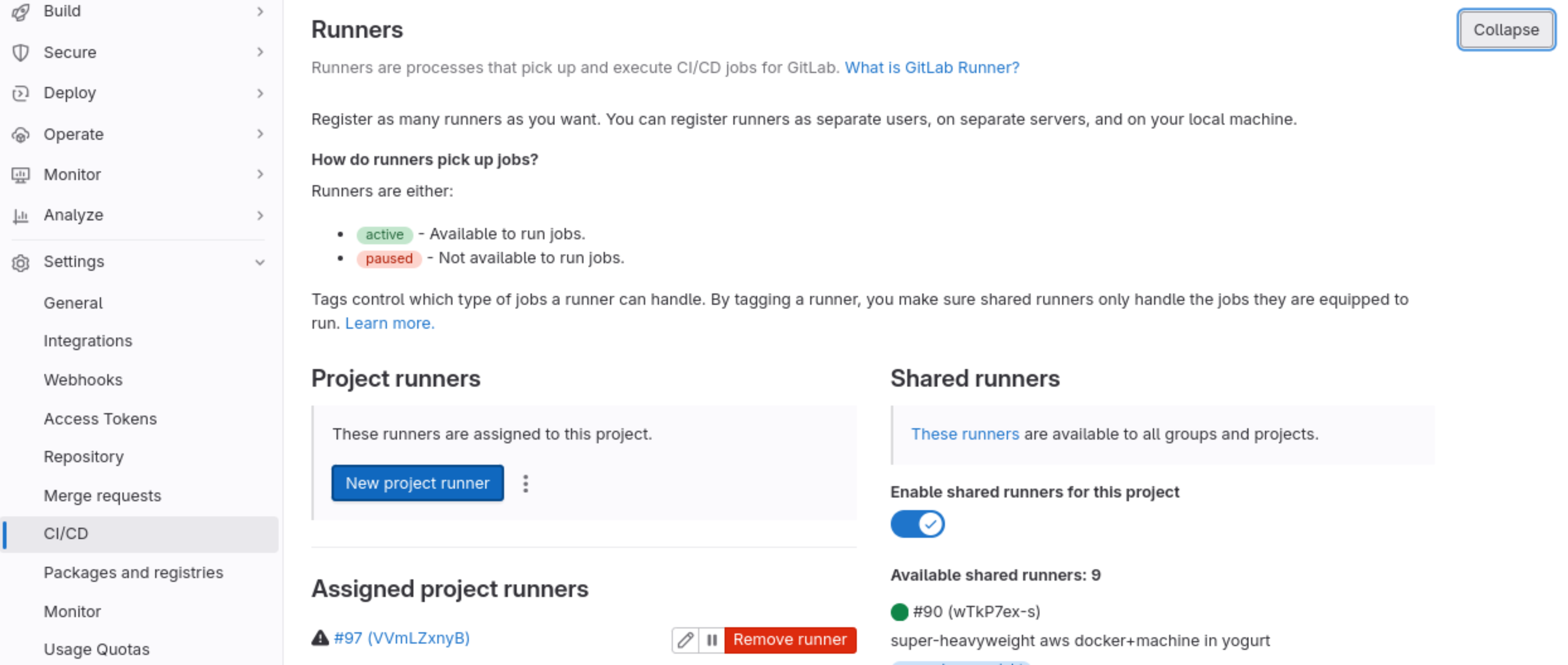
- Documentation/ci/gitlab-ci/images/new-project-runner.png 0 additions, 0 deletionsDocumentation/ci/gitlab-ci/images/new-project-runner.png
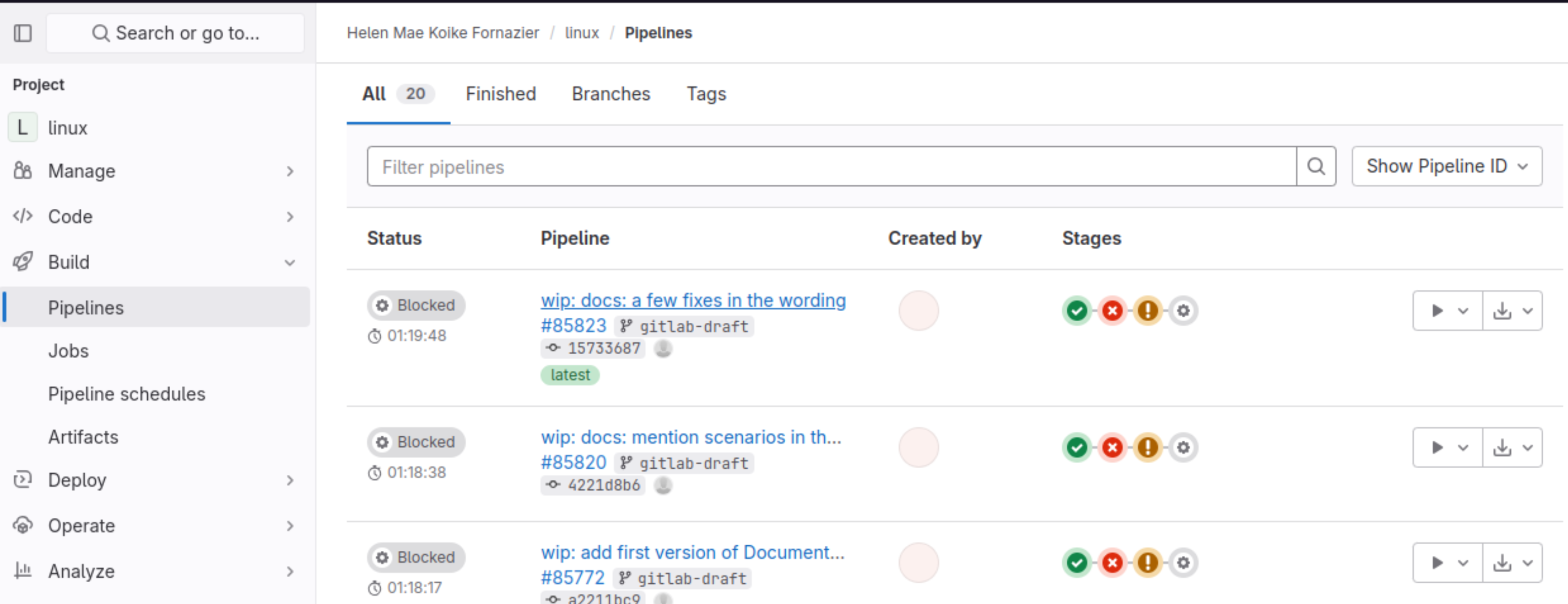
- Documentation/ci/gitlab-ci/images/pipelines-on-push.png 0 additions, 0 deletionsDocumentation/ci/gitlab-ci/images/pipelines-on-push.png
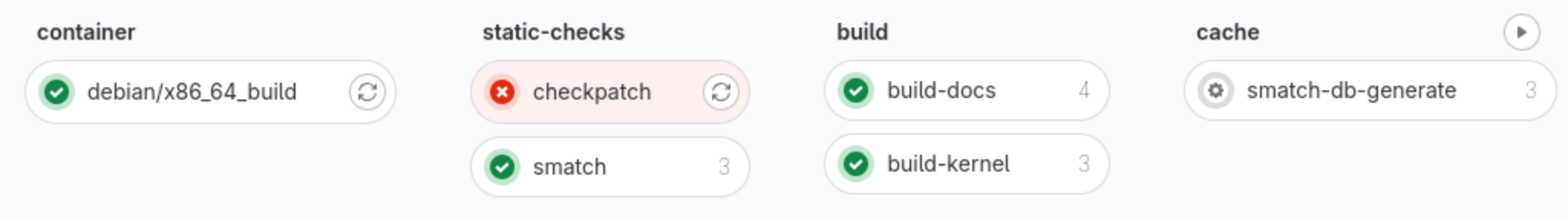
- Documentation/ci/gitlab-ci/images/the-pipeline.png 0 additions, 0 deletionsDocumentation/ci/gitlab-ci/images/the-pipeline.png
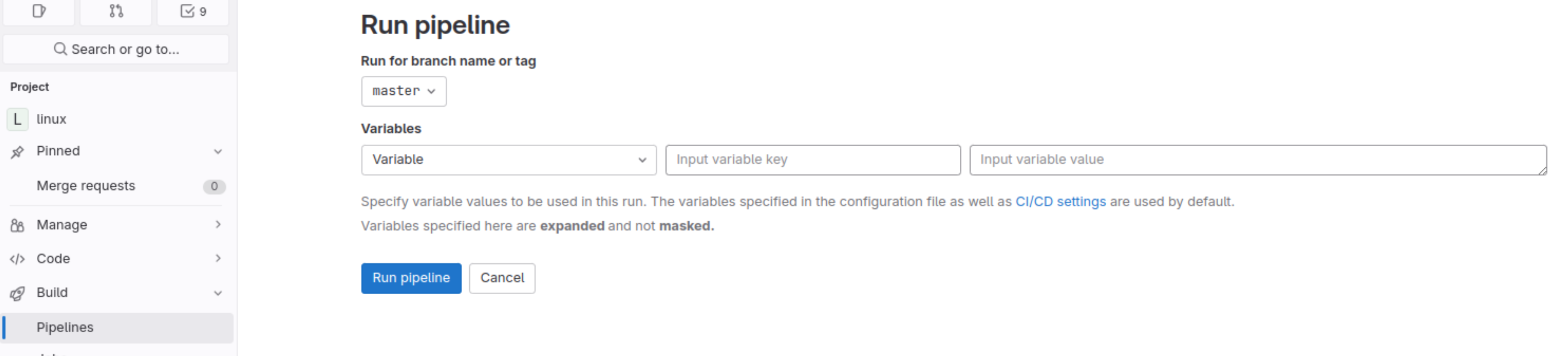
- Documentation/ci/gitlab-ci/images/variables.png 0 additions, 0 deletionsDocumentation/ci/gitlab-ci/images/variables.png
- MAINTAINERS 8 additions, 0 deletionsMAINTAINERS
- ci/gitlab-ci/bootstrap-gitlab-runner.sh 54 additions, 0 deletionsci/gitlab-ci/bootstrap-gitlab-runner.sh
- ci/gitlab-ci/ci-scripts/build-docs.sh 34 additions, 0 deletionsci/gitlab-ci/ci-scripts/build-docs.sh
- ci/gitlab-ci/ci-scripts/build-kernel.sh 34 additions, 0 deletionsci/gitlab-ci/ci-scripts/build-kernel.sh
- ci/gitlab-ci/ci-scripts/ici-functions.sh 100 additions, 0 deletionsci/gitlab-ci/ci-scripts/ici-functions.sh
- ci/gitlab-ci/ci-scripts/install-smatch.sh 13 additions, 0 deletionsci/gitlab-ci/ci-scripts/install-smatch.sh
- ci/gitlab-ci/ci-scripts/parse_commit_message.sh 25 additions, 0 deletionsci/gitlab-ci/ci-scripts/parse_commit_message.sh
- ci/gitlab-ci/ci-scripts/run-checkpatch.sh 19 additions, 0 deletionsci/gitlab-ci/ci-scripts/run-checkpatch.sh
- ci/gitlab-ci/ci-scripts/run-smatch.sh 44 additions, 0 deletionsci/gitlab-ci/ci-scripts/run-smatch.sh
- ci/gitlab-ci/docker-compose.yaml 18 additions, 0 deletionsci/gitlab-ci/docker-compose.yaml
- ci/gitlab-ci/yml/build.yml 43 additions, 0 deletionsci/gitlab-ci/yml/build.yml
- ci/gitlab-ci/yml/cache.yml 26 additions, 0 deletionsci/gitlab-ci/yml/cache.yml
- ci/gitlab-ci/yml/container.yml 36 additions, 0 deletionsci/gitlab-ci/yml/container.yml
.gitlab-ci.yml
0 → 100644
Documentation/ci/gitlab-ci/gitlab-ci.rst
0 → 100644
156 KiB
593 KiB
520 KiB
89.5 KiB
271 KiB
ci/gitlab-ci/bootstrap-gitlab-runner.sh
0 → 100755
ci/gitlab-ci/ci-scripts/build-docs.sh
0 → 100755
ci/gitlab-ci/ci-scripts/build-kernel.sh
0 → 100755
ci/gitlab-ci/ci-scripts/ici-functions.sh
0 → 100644
ci/gitlab-ci/ci-scripts/install-smatch.sh
0 → 100755
ci/gitlab-ci/ci-scripts/run-checkpatch.sh
0 → 100755
ci/gitlab-ci/ci-scripts/run-smatch.sh
0 → 100755
ci/gitlab-ci/docker-compose.yaml
0 → 100644
ci/gitlab-ci/yml/build.yml
0 → 100644
ci/gitlab-ci/yml/cache.yml
0 → 100644
ci/gitlab-ci/yml/container.yml
0 → 100644